Feature Introduction: Restricting Data Traffic with Port Isolation

Author: Jonas Gesch
Job Title: Field Application Engineer
Communication within Operational Technology (OT) networks typically needs to be reliable and secure to ensure correct operation and avoid downtimes. It is therefore extremely important, especially in safety-critical networks, to shield Ethernet communication from external influences that could disrupt connectivity and to make sure that confidential data is not accessible by devices outside of the trusted network.
In recent times, Industry 4.0 has driven an ever-higher demand for availability of data to monitor and analyze systems in real-time. To meet this demand, industrial applications have moved increasingly closer to the convergence of IT and OT networks. Linking those two networks, which have been historically separated, allows IT software to retrieve data directly from end-devices like machines on a factory floor, but it also exposes them to many new cyber-threats they were never designed to face. Another potential risk originates from within the OT network, where accidentally connecting a malfunctioning device could cause communication to break down or a malicious actor gaining access to an unprotected switch port could perform targeted attacks to intercept confidential data.
.png)
Figure 1: Potential Risks to Critical Devices
So what can be done to minimize the risks for the most mission-critical devices in your network? The most effective way to increase security is to restrict the connections to critical devices. In a layer 2 network, data can be exchanged between all devices in the same broadcast domain by default. Controlling the data flow to a trusted part of the network by restricting which devices can send data to or receive data from a critical device significantly decreases the attack surface. This can be achieved to some extent with VLANs, which separate a network into multiple VLAN domains where data can only be exchanged between devices within the same VLAN. However, VLAN configuration can quickly become very complicated and requires careful planning, documentation and maintenance for every device in the network.
Compared to VLAN, Port Isolation offers a much simpler method of restricting ingress or egress data flow between individual ports of an Ethernet switch. It is also possible to use Port Isolation in conjunction with VLANs to further restrict the communication of devices within the same VLAN. Its easy configuration and effectiveness make it a valuable tool to hardening network security by restricting communication to trusted connections.
In OT networks, port isolation limits unnecessary device-to-device communication, reducing the risk of lateral movement and malware spread. It ensures HMIs, engineering stations, and vendor devices only access designated controllers, contains legacy systems with limited security, and helps maintain safety and availability by preventing unintended traffic or disruptions in real-time control.
The main purpose of Port Isolation is to forward data packets only to ports where they are intended to be received. This foremost provides advantages regarding network security, but also has other benefits, which can be summarized as follows:
Port Isolation is a feature enforced on Ethernet switches and operates on layer 2 of the OSI model (data link layer). The underlying method is that communication between individual ports of the switch is either forwarded or blocked. When a connection between two ports is blocked, those are considered as “isolated” from each other. Some vendors only allow to configure an uplink port, which can communicate with all downlink ports on the switch. Traffic between all downlink ports is then isolated so that they can only communicate through the uplink port. This horizontal segregation is often also referred to as Private VLAN and is useful for applications like a guest network in a hotel where customer devices should not be allowed to communicate directly.
Volktek offers a more advanced version of Port Isolation where the connection between any two ports of the switch can be isolated individually, offering more flexibility for configuration and specific networking needs. For this reason, the following sections of the article refer to this more advanced implementation of Port Isolation. In the example of Figure 2 below, ports 1-3 can communicate freely amongst each other while port 4 can only exchange data with port 1 and is isolated from all other ports. Port 5 can only transmit data to port 3 without receiving any data and port 6 can only receive data from port 3, but not transmit any data. The ports 7 to 10 are completely isolated from all other ports and therefore unused.
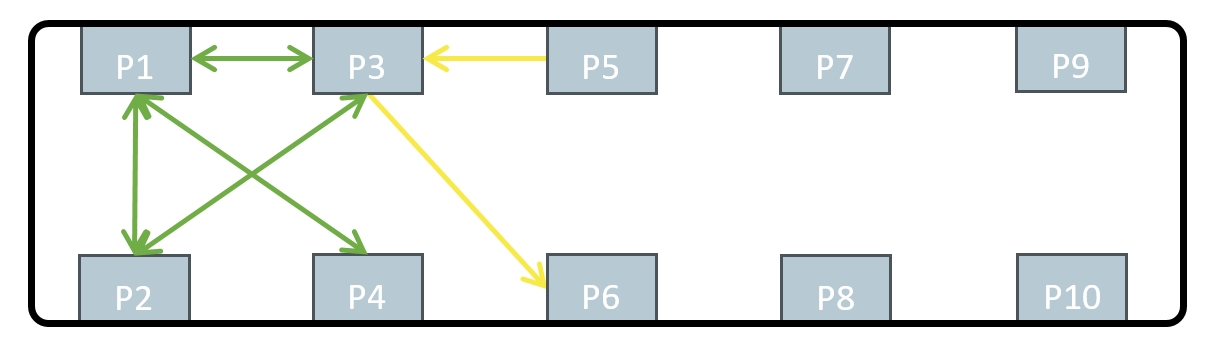
Figure 2: Example of Port Isolation on an Ethernet Switch
Configuring Port Isolation in the Web GUI is a straight-forward process and requires only few steps, which are explained in more detail below, using the Volktek Web GUI as an example. Settings can be changed for individual ports or a range of ports at the same time as can be seen in Figure 3. Packets received on those ports will be forwarded to all Egress Ports which are selected below. Selecting Port 0 means that the packets will also be forwarded to the switch CPU, which is necessary for management access to the Ethernet switch and features like SNMP. This means that it is also possible to restrict management access for this switch with Port Isolation to specific ports without needing to change management VLAN settings.
Note: At least one port still needs to have port 0 enabled as Egress Port or management access to the switch via the Ethernet interface will be lost.
.png)
Figure 3: Port Isolation Configuration Interface
The resulting settings are visualized in the matrix displayed in Figure 4. Referring back to the example in Figure 1, the table shows that packets received on ports 1-3 are forwarded to each other as well as the switch CPU and port 3 additionally forwards to port 6. Port 4 forwards to and receives from port 1 while port 5 only forwards to port 3.
.png)
Figure 4: Port Isolation Settings
Q1. What is Port Isolation?
A: Port Isolation is a Layer 2 Ethernet switch feature that restricts data forwarding between ports, allowing traffic only to explicitly permitted ports.
Q2. What problem does Port Isolation solve in industrial networks?
A: It protects critical devices by preventing unintended or unauthorized device-to-device communication, reducing the risk that a compromised, malfunctioning, or misconnected device can disrupt or access critical systems within OT networks.
Q3. How is Port Isolation different from VLANs?
A: VLANs separate devices into different broadcast domains, but allow unrestricted communication within the same VLAN. Port Isolation restricts communication between individual ports, even when those ports belong to the same VLAN.
Q4. Can Port Isolation be used together with VLANs?
A: Yes. Port Isolation can be applied within a VLAN to further restrict communication between devices that must share the same VLAN for operational reasons.
Q5. What are common use cases for Port Isolation?
A: Typical use cases include protecting safety-critical devices, isolating field devices on factory floors, securing guest or temporary connections, and limiting lateral movement in converged IT/OT networks.
Q6. Can Port Isolation restrict management access to the switch?
A: Yes. By controlling whether traffic is forwarded to the switch CPU (often referred to as port 0), management access can be limited to specific physical ports.
Q7. Can Port Isolation protect against malware or ransomware?
A: Port Isolation does not detect malware, but it limits lateral movement, reducing the ability of malicious software to spread between devices on the same switch.
Q8. Does Port Isolation affect network performance or latency?
A: No. Port Isolation is enforced in switch hardware and does not introduce additional latency or throughput limitations.
Volktek Corporation is a Taiwan-based manufacturer specializing in industrial Ethernet networking solutions with more than three decades of experience in supporting industrial automation, building management system, maritime, transportation, energy, and critical infrastructure applications. Volktek focuses on delivering reliable, secure, and easy-to-deploy networking products that operate consistently in harsh industrial environments.
With in-house design, manufacturing, and quality control, Volktek supports customers worldwide through the full product lifecycle—from system design and deployment to long-term operation and technical support. Our portfolio emphasizes robustness, long product availability, and practical security features to help customers build resilient and future-ready OT networks.