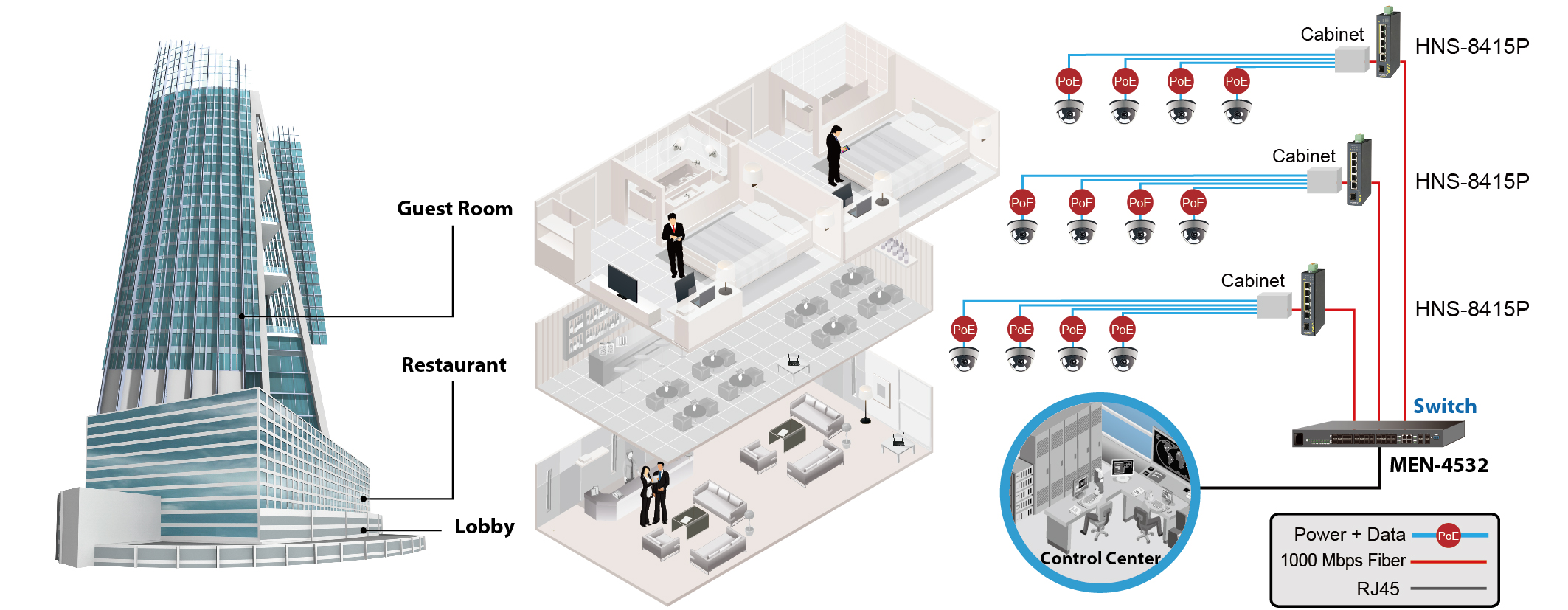
Application Overview
To protect and service their clients and staff, hotels needs to incorporate the following network system in their facility:
Key Considerations
Key Volktek Benefits
| Feature | Benefit | ||
| Reliability | Front Power Access | Easy Operation | Provides an easy method to connect power and service the device when installed in the rack. |
| Reliability | Redundant Power | Remains On During Power Failure | Redundant power sources (15VDC or battery back-up) keep the devices operational during power failures. |
| Reliability | Multi-rate Fiber Port | Auto Uplink and Downlink Rate Negotiation | The multi-rate switches check the speed of the network and set the uplink/downlink speeds accordingly to optimize their performance in the data transmission. |
| Availability | Ring Redundancy | Remains Connected If Active Link Fails |
1) Rapidly react to physical link failure and recover immediately 2) Provide an alternate pathy link to support continuous transmission. |
| Performance | Storm Control | Prevent LAN Traffic Storms | Prevents the traffic on a LAN from being disrupted by a broadcast, multicast, or unicast storm on a port. A managed network optimizes the overall traffic capacity, reducing the system bandwidth requirements and saving CAPEX. |
| Security | Port-security and DHCP Snooping | Limit Incoming Traffic and Identify Trusted Sources | Port security sets the maximum number of MAC addresses per interface. When the limit is exceeded, incoming packets with new MAC addresses are dropped. This prevents new devices from being added from increasing the network traffic. DHCP Snooping acts like a firewall between untrusted hosts and DHCP servers. It maintains a binding table to identify the trusted and untrusted servers and uses it to check packets from untrusted interfaces. |
| Security | Access Control List (ACL) | Additional Security with Controlled Network Traffic | Create filter rules for forwarding specific packets or denying network access. Network administrators use it to filter traffic and provide an extra layer of network security. |
| Management | e-mail Alarm | Triggered events alert via e-mail |
1) Notify the administrator if real-time problems occur such as firmware or configuration changes, device status, link connectivity status, etc. 2) Help administrators to quickly identify, isolate and resolve network issues. |
Application Diagram